Digitally Signing and Encrypting E-mails
This post is going to dial the nerd meter back a significant amount to go into the finer details of a very common technology that I suspect many people don’t quite understand. My hope is that some of the power users read this to get a better understanding of the technology they use every day, and the admins who don’t quite “get it” will have some of the dots connected.
You click to open up a new e-mail and you see the somewhat obscure red ribbon and the blue lock (pictured above). The red ribbon is to digitally sign, and the blue lock is to encrypt.
Digitally signing an e-mail tells the person you sent the e-mail to that it was definitely sent from you. It’s a lot like one of those certificates of authenticity you get when you buy autographed sports memorabilia. In technical terms, by digitally signing an e-mail you are providing integrity and nonrepudiation. Integrity means that your e-mail cannot be modified between you are the person you are sending to, and nonrepudiation means you cannot deny sending the e-mail. When you go through your annual corporate information assurance training, there is likely to be a bunch of illustrations about how you should only click on hyperlinks from digitally signed e-mails. This is because since the digital signature gives you integrity and nonrepudiation, you know the e-mail is sent by the person you thought it was, and you know the hyperlink wasn’t altered by some hacker to send you to a malicious site. What many people confuse is that digitally signing an e-mail DOES NOT grant confidentiality. Said another way, digitally signed e-mails can still be intercepted and read by a malicious party, they just can’t be altered. Another frequent misconception is that a digital signature is not a digital version of what it looks like when you write your name. It is also not the last few lines of your e-mail where you have your name, phone number, e-mail address, etc.
Encrypting an e-mail ensures that only the person (or people) that you want to read your e-mail, and ONLY those people, are able to read the e-mail. By keeping your information restricted to only those who are authorized to view it, you are maintaining confidentiality. You specifically want to encrypt an e-mail when you are passing information that is sensitive. An example of appropriate information for encryption would be one of those strange cases where some arcane system needs your, or one of your subordinates, full SSN. This is not something you would want to send in the clear. It is NOT appropriate to send information of another classification – ie. even if you encrypt the e-mail, you can’t send secret data from an unclassified e-mail address. ***QUICK RANT*** Don’t be THAT guy/gal who encrypts every e-mail you send. You are not being security conscious, you are being obnoxious. If this is you, stop it right now.
This all sounds wonderful, but I am guessing there are a couple doubters out there, and maybe a couple of people who “just want to know how it works”. Here goes. Both digital signatures and encryption rely on asymmetric cryptography. Unlike symmetric cryptography where the same key is used for encryption and decryption, asymmetric cryptography uses key pairs. These pairs of keys are comprised of a public key and a private key. As you certainly could guess by the name, the public key can, and should, be made available. The private key needs to be protected and only available to the owner. If something is encrypted using one key, it can only be decrypted using the other key. An example would be, if I encrypted a message using Paul’s public key, I would know that only Paul would be able to decrypt and read the message, because the only thing that could decrypt that message would be Paul’s private key (which theoretically only Paul would have). Another concept you need to understand is a hash. A hash is a numerical value used to represent a data set. A hash is used to tell you if something was corrupted in transit. Your e-mail is hashed so the system will know if part of the message was lost. Hashes are one-way functions, which means on the receiving end your hash is not un-hashed, it is actually hashed a second time and the received info’s hash is compared to the original hash. If the two values match, nothing was lost. If they don’t match, you know your message is corrupted.
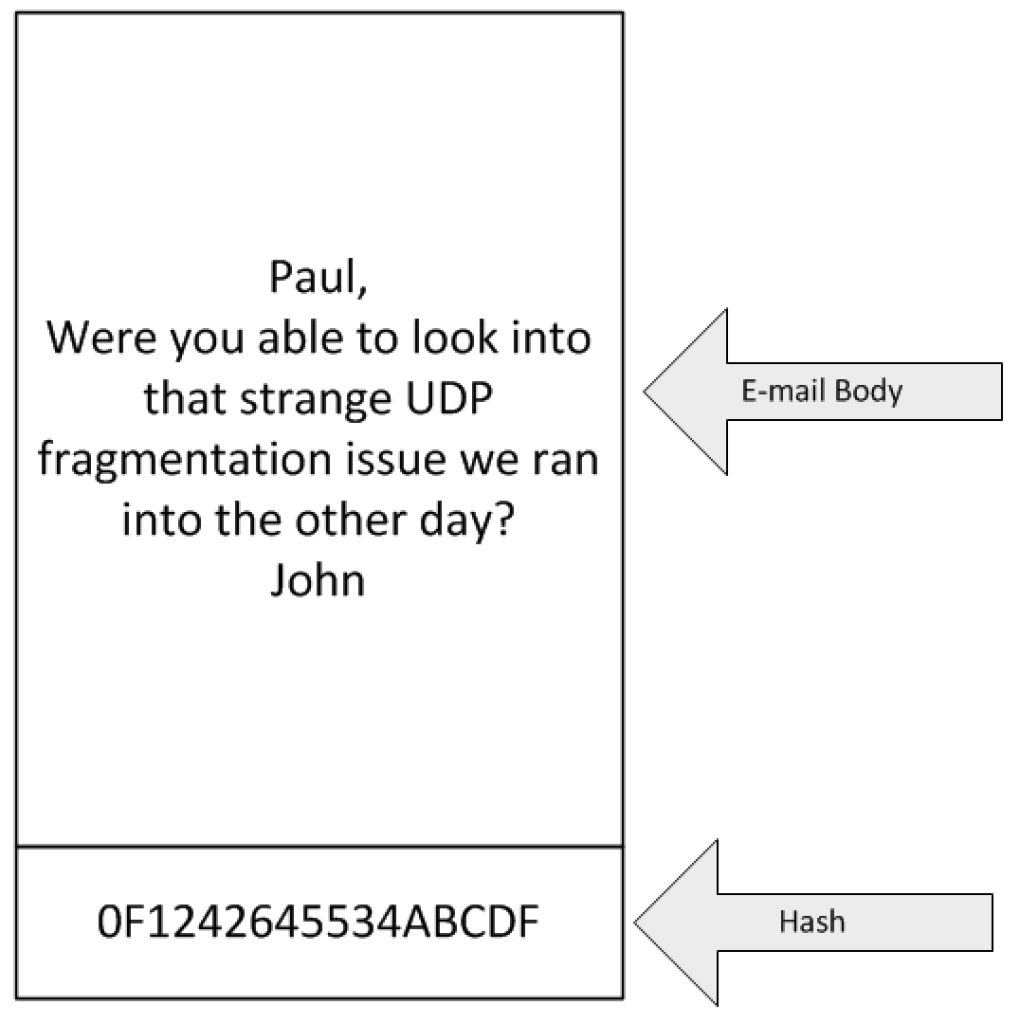
The graphic above shows a depiction of what an e-mail “looks” like, so we can go into how the look changes when using digital signatures and/or encryption.
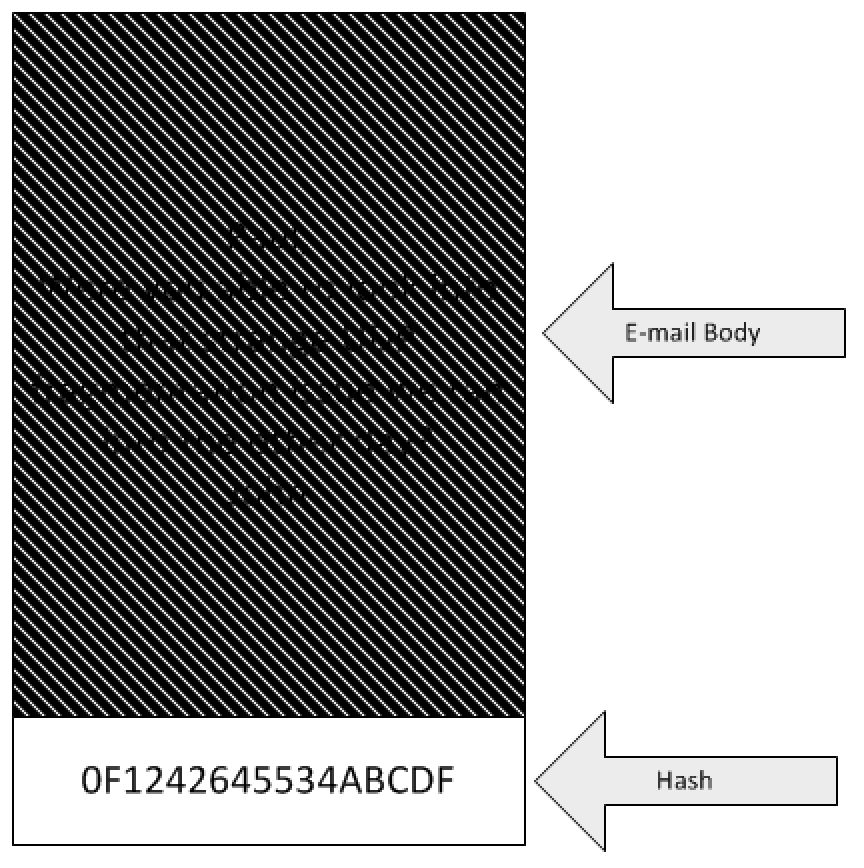
The above picture shows you what it looks like when you encrypt an e-mail. You can’t see the body of the e-mail unless you are the person the e-mail is sent to. The e-mail is encrypted using the private key of the person you are sending the e-mail to. In this case, John sent an e-mail to Paul, so only Paul’s private key can decrypt it. This e-mail WILL be confidential, because only Paul can read it. Anyone with access to Paul’s public key could have sent the e-mail, so there is no assurance in regards to who sent the e-mail.
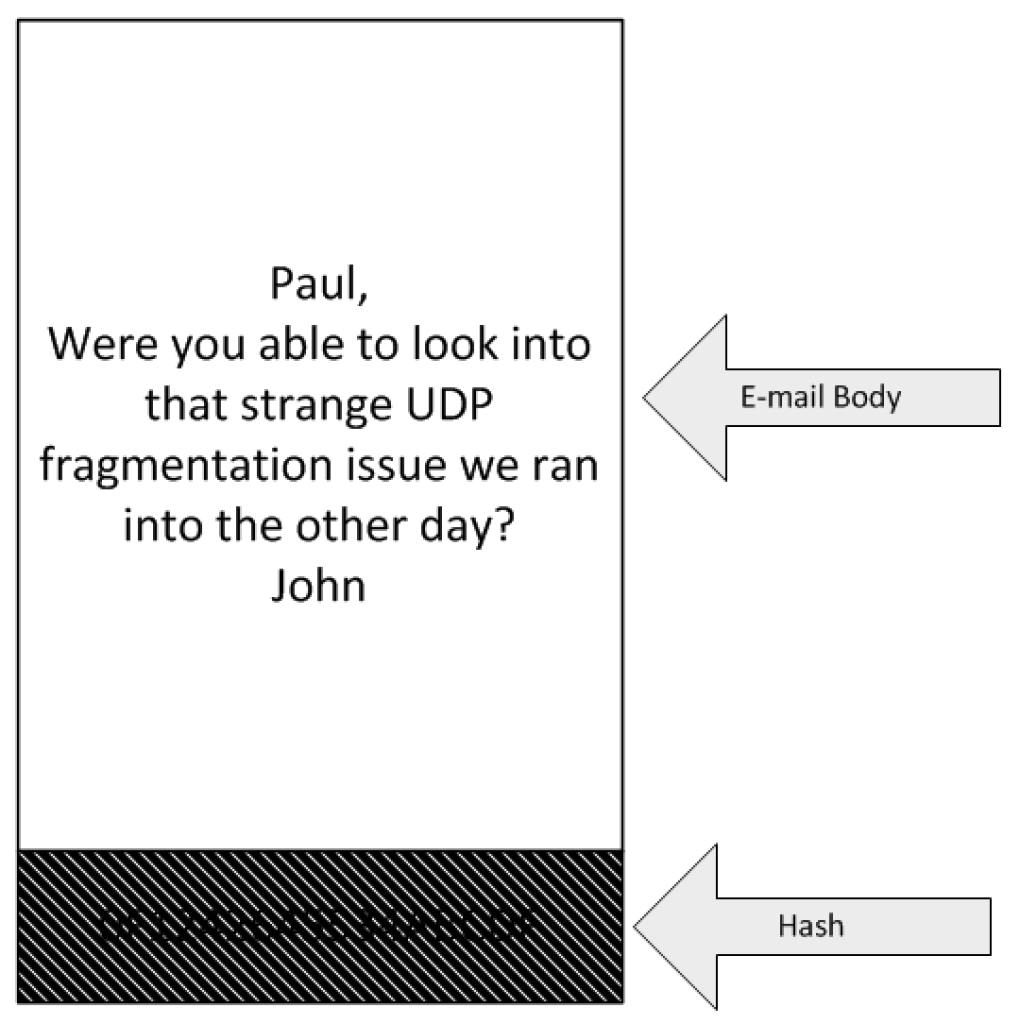
The above picture shows you what it looks like when you digitally sign an e-mail. It won’t stop anyone from reading your e-mail, so it doesn’t give you confidentiality. The hash is encrypted, so while you are able to read the e-mail, you won’t be able to alter it. Additionally, because the hash is encrypted using the sender’s private key, you can be assured only that person could have sent the e-mail. In this case, this means that we are certain John sent the e-mail to Paul.
If you need to make sure you can verify the sender of an e-mail AND you need to make sure no one but your intended recipient can read it, you can both encrypt AND digitally sign the e-mail.